Image Gallery Lightbox
The title of the gallery




✖
![]()
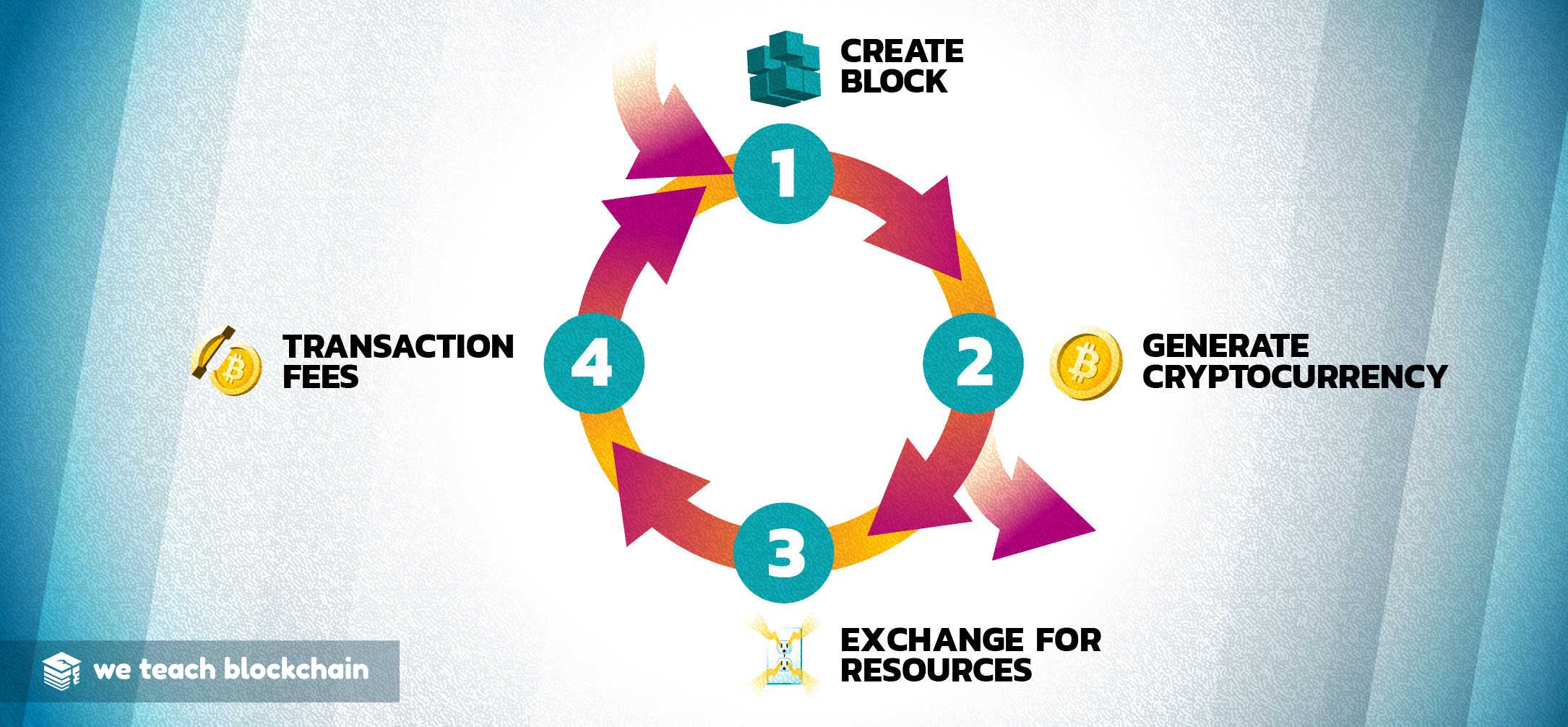
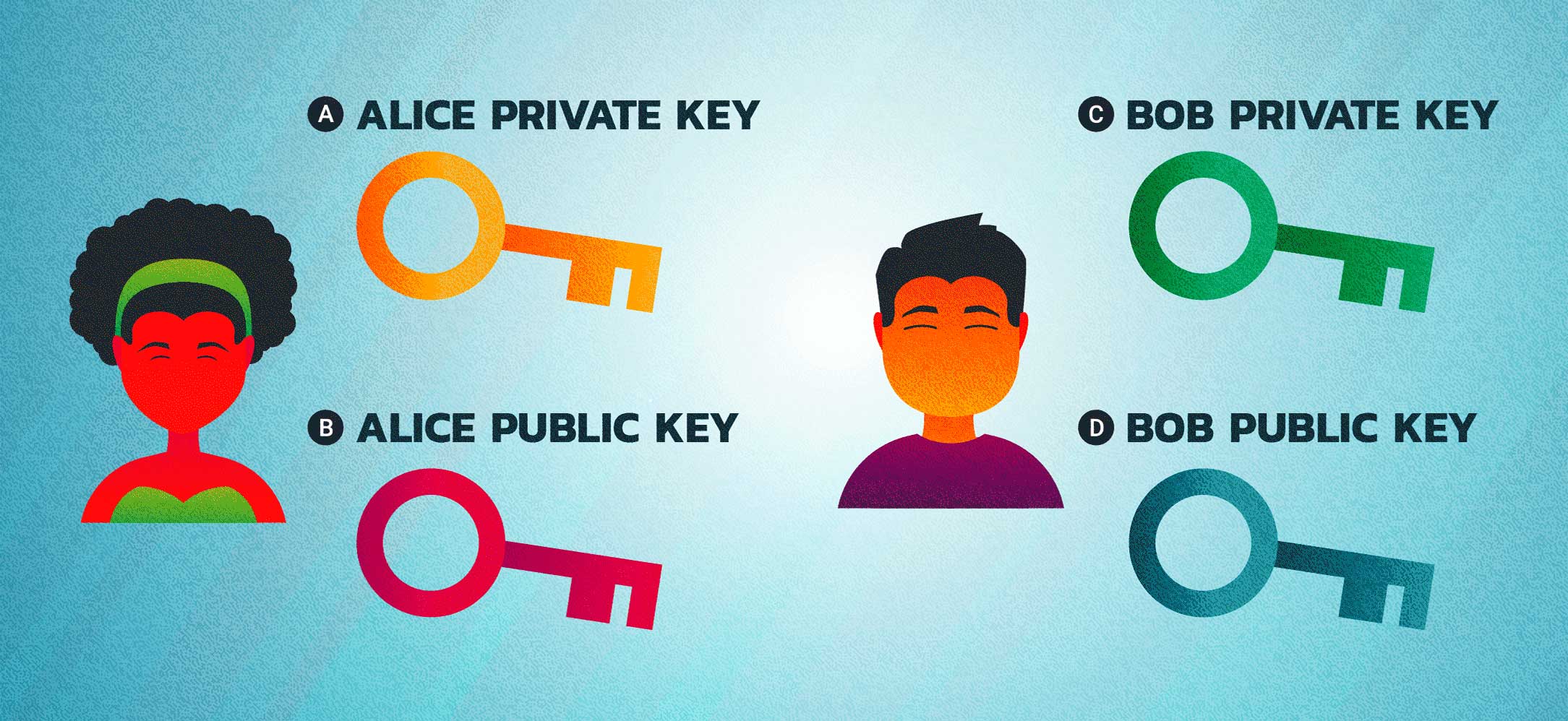
The section below shows mock ups of all of the components which can be used on FAQ and lesson pages.